It is important to define the various levels of access to an information technology system individuals require. The levels of access given to individuals are determined on two primary factors:
- The individual's role within the organization.
- The sensitivity of the information being stored on the system.
Privilege is the authority to make changes to a system. Both people and accounts can have privileges, and both can have different levels of privilege.
For example, an IT administrator or “super user” may be able to configure servers, firewalls, and cloud storage, and has a high level of privilege. A sales rep, however, should be able to use some systems but they shouldn’t be able to change network settings, permissions, or download software unless it’s on an approved list.
Privileged is an adjective that describes things with privilege (e.g. privileged account, privileged identity).
for example when someone says “That account has privilege,” means it has a higher level of access and permissions than a standard account. One could also say, “That is a privileged account.”
In the example of the administrator role, although the admin has a certain level of privilege he or she still needs a privileged account in order to perform privileged tasks.
Two key concepts are used to assign and manage the access rights of individuals, two key concepts are used: Privileged Identity Management (PIM) and Privileged Access Management (or PAM for short).
PIM
According to Oxford Computer Training, Privileged Identity Management can be defined as follows:
“Privileged Identity Management (PIM) is a capability within identity management focused on the special requirements of managing highly privileged access.
PIM is an information security and governance tool to help companies meet compliance regulations and to prevent system and data breaches through the improper use of privileged accounts.”
PAM
PAM is an acronym that stands for:
Privileged Account Management or Privileged Access Management
Privileged Access Management
includes all security strategies and tools that enable organizations to manage elevated access and approvals for users, accounts, applications, and networks.
In a nutshell, PAM lets companies limit their attack surface by granting a certain level of privileged access, thus helping them avoid and minimize the potential harm that may result from external or internal threats.
Here is a definition of PAM provided by TechTarget:
“Privileged access management (PAM) is the combination of tools and technology used to secure, control and monitor access to an organization’s critical information and resources. Subcategories of PAM include shared access password management, privileged session management, vendor privileged access management and application access management.”
Privileged Account Management
is part of Identity and Access Management, focused on safeguarding an organization’s privileged accounts.
IAM

Identity and Access Management recognizes the need to enable adequate access to services and to satisfy stringent regulatory required standards. IAM is a vital endeavor in every organization, requiring technological competence and a high-level understanding and overview of the business. Here’s how Gartner defines Identity and Access Management:
“Identity and access management (IAM) is the discipline that enables the right individuals to access the right resources at the right times for the right reasons.”
Before discussing security models further, let's recall the three elements of the CIA triad: Confidentiality, Integrity and Availability. We've previously outlined what these elements are and their importance. However, there is a formal way of achieving this.
The Bell-La Padula Model
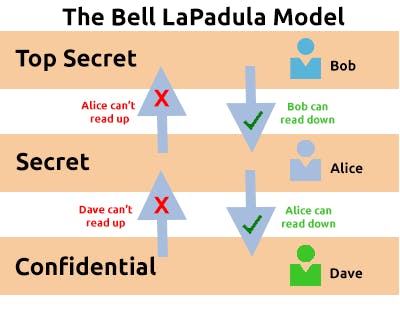
The Bell-La Padula Model is used to achieve confidentiality. This model has a few assumptions, such as an organisation's hierarchical structure it is used in, where everyone's responsibilities/roles are well-defined.
The model works by granting access to pieces of data (called objects) on a strictly need-to-know basis. This model uses the rule "no write down, no read up".
Properties of Bell-LaPadula Model
- The Simple Security Property (No Read Up) The Simple Security Property states that, “A subject at a given security level may not read an object at a higher security level”.
- The Star Property (No Write Down) The Star Property states that, “A subject at a given security level may not write to any object at a lower security level”.
- The Strong Star Property The Strong Star Property states that, “A subject can perform read & write capabilities only on those functions present at the same security level”. ( i.e A subject in one classification level cannot read or write to any other classification level)
Advantages :
This model resists Trojan horse attack. Since, this the model focuses on confidentiality & controlled access to classified information, it is used in military & mission critical applications.
Disadvantage : Bell-LaPadula model emphasizes only confidentiality; does not address the issue of data integrity.
The Bell LaPadula Model is popular within organizations such as governmental and military. This is because members of the organizations are presumed to have already gone through a process called vetting. Vetting is a screening process where applicant's backgrounds are examined to establish the risk they pose to the organization. Therefore, applicants who are successfully vetted are assumed to be trustworthy - which is where this model fits in.
Biba Model
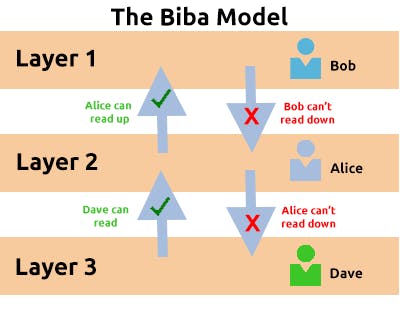
The Biba model is arguably the equivalent of the Bell-La Padula model but for the integrity of the CIA triad.
This model applies the rule to objects (data) and subjects (users) that can be summarised as "no write up, no read down". This rule means that subjects can create or write content to objects at or below their level but can only read the contents of objects above the subject's level.
Properties of Biba Model
- The Simple Integrity Property (No Read Down) A subject at a given level of integrity must not read data at a lower integrity level
- The Star Integrity Property (No Write Up) A subject at a given level of integrity must not write to data at a higher level of integrity
- Invocation Property A subject at one level of integrity cannot cannot request access to a subject at a higher level. (Only with subjects at an equal or lower level)
Advantages : This model is simple & easy to implement.
Disadvantage : It does not enforce confidentiality.
The Biba model is used in organizations where integrity is more important than confidentiality. For example, in software development, developers may only have access to the code that is necessary for their job. They may not need access to critical pieces of information such as databases, etc.

![Information Security Series: [Part2] Principles of Privileges](https://cdn.hashnode.com/res/hashnode/image/upload/v1647290198557/daFz7fDND.png?w=1600&h=840&fit=crop&crop=entropy&auto=compress,format&format=webp)