Table of contents
In this series, we are going to talk about the basic principles of information security & the fundamental frameworks that are used to protect data and systems.
The CIA Triad
In 1998 a security model called the CIA triad started being used for creating security policies. Information security doesn't start and/or end with cyber security, but instead it applies to a lot of scenarios like record keeping, storage of information etc.
the CIA triad consists of three sides: Confidentiality, Integrity and Availability (CIA). this model quickly became an industry standard. This model also determines the value of data it applies to and in turn, the attention it requires from business.
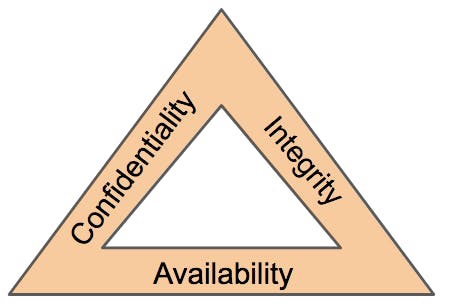
The CIA triad is different in that instead of being divided into different sections, it is instead a continuous cycle. its sides can overlap and if just one side is not satisfied, the other two are useless (like a triangle). if a security policy doesn't work on the three sections it cannot be considered an effective policy.
Confidentiality
This side of the triad focuses on protecting the data from unauthorized access and misuse. Any organization has some sort of sensitive data/system that it needs to protect from parties that are not intended to view / edit.
Integrity
This side cares about keeping information accurate and consistent unless authorized changes are made. information can be become inaccurate due to careless change, errors, or unauthorized access. in the CIA triad model, integrity is achieved when information remains unchanged during transportation, storage, and usage not requiring modification of data.
Availability
In order for data to have value and be useful, it must be available and accessible by the user when authorized users need it. Availability is a very important part of SLA (Service Level Agreements). You often hear statements like: the system is 99.99% available.
As you might see, the three sides of the triad indeed form a continuous cycle, missing or ignoring any of them will make the two others useless.
In the next post we will talk about the standard principles around Privallages.

![Information Security Series: [Part1] Principles of Security](https://cdn.hashnode.com/res/hashnode/image/upload/v1647209120646/xVK4QYmwq.png?w=1600&h=840&fit=crop&crop=entropy&auto=compress,format&format=webp)