In this article I will be talking about the basic concepts that are used within a Blockchain.
Hash Functions
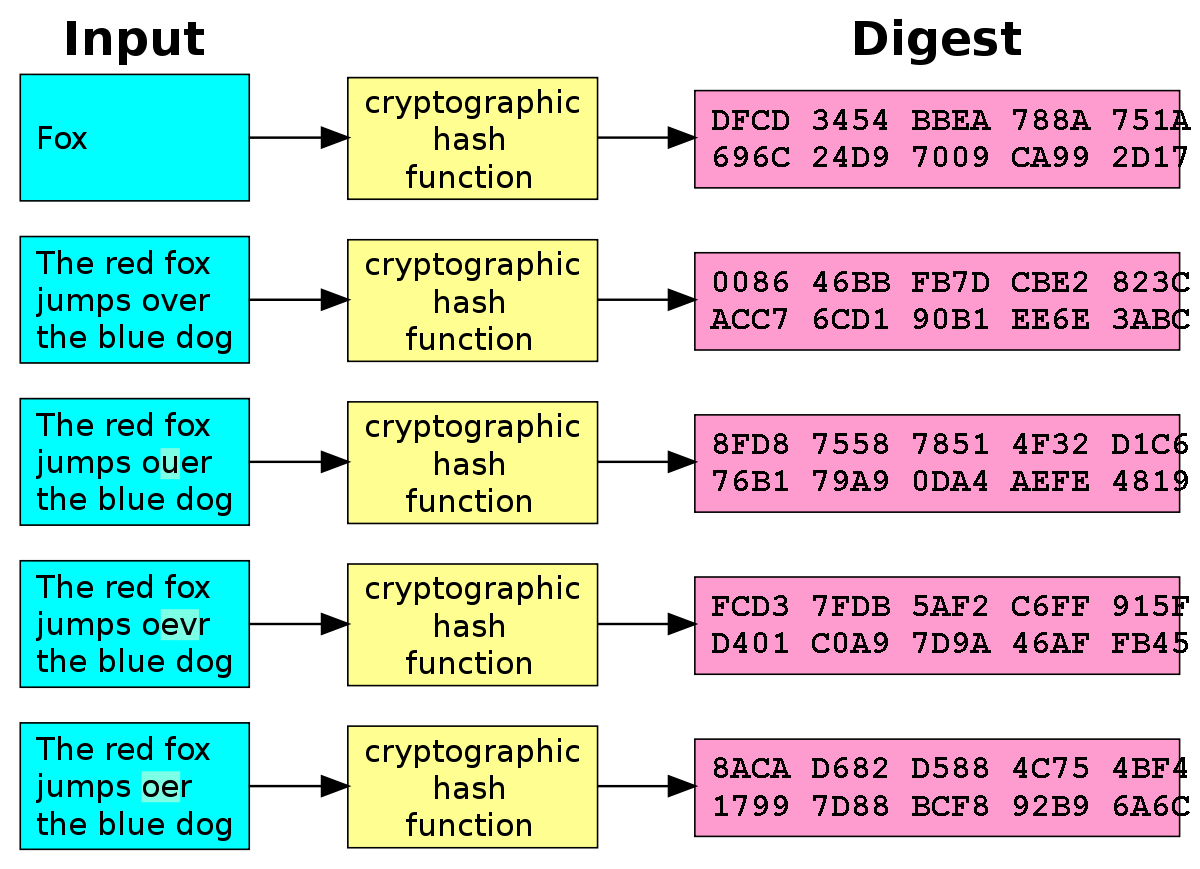
A hash function is any function that can be used to map data of arbitrary size to fixed-size values. The values returned by a hash function are called hash values, hash codes, digests, or simply hashes.
A good hash function that acts of data: X should have the following properties :
- No other X’ can have HASH(X’) equal to Y. Its one to one mapping.
- The size of Y is fixed and the size of X can be arbitrary.
- Given Y you can not calculate X. Its a one-way function!
- If I change even 1 bit of the data, the computed digest should change.
This basically mean that I can take any chunk of data and compute its unique digest using a hash function. If I send that piece of data and its computed hash along with it to a receiver, Bob, Bob can then recompute the hash of the data received to ensure that the content of was not corrupted in the transmission. When we download a file from the internet, it uses the same hash functions to verify its integrity. most of the files you will download from the internet nowadays will be accompanied with hashes to allow you to check for their integrity.
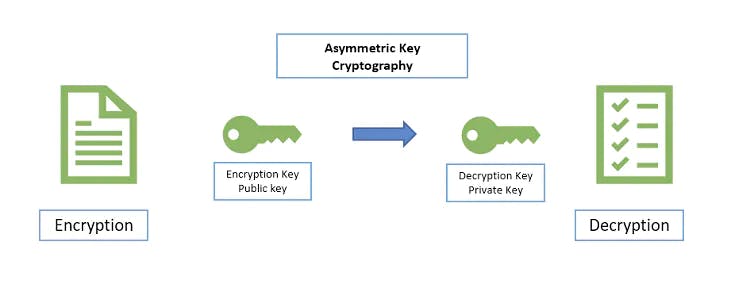
Asymmetric Cryptography
In the digital world there is primarily two types of encryption: symmetric & asymmetric. In Symmetric encryption there is a single secret key that is used for both encrypting & decrypting of data. it is like your home keys for example. any one with a copy can lock / unlock your door.
Asymmetric encryption on the other hand works in a quite different way. you have a set of two keys, a locking key and an unlocking key. or can be called public & private key. you can lock your door with the either of the keys, but you can only unlock it with the other key. this means if you have the one of the keys only you can lock stuff up but only a person with the other key in the set can unlock it.
these in the computer world are called public and private keys.
Secure Communication using Public Key Cryptography
Now in order to communicate securely you can use this concept of Asymmetric encryption as follows:
- You and other party both have public and private keys
- You both share with each other the public (locking keys)
- When you want to send something you lock it with the other party locking key.
- other party decrypts the message by its private (unlocking) key.
- Other party prepares response, locks it by your public (locking key).
- Because you are the only one with the unlocking key you are the only entity that can unlock other party response.
In this scheme the locking keys (public) can be shared on the internet without any problem as only secret keys can be used for message decryption 😂.
Digital Signatures using Public Key Cryptography
Let’s continue with the previous communication example. Where you receives a message, which when you decrypts says “Meet me at 11:00 tomorrow”. How can you know for sure that the message was sent by the other party and not a malicious entity?
This can be achieved if the message is “signed” by its sender. you as a receiver receiver of the message can then verify the signatures.

If we don't need to encrypt the whole message, one way to “digitally sign” the message is as follows:
- The sender to calculate the hash of the message data.
- Sender encrypt this hash with its private key and sends it with the message.
- Receiver gets the message and calculates its hash on its own.
- Receiver can decrypt the hash sent by the sending party using its public key.
- If the message was indeed a legit message the decrypted hash would match the hash calculated by the receiver.
Public Key Infrastructure
For the entire secure communication to work, both parties need to establish trust in each other’s public key while using the same open unsafe internet. The question now is how to share the key and prove its ownership to ensure future secure communication? if there is no way to link the public key to an entity any entity can simply announce a public key and claim to be anybody and thus breaking security.
To help solve this issue we have a concept of a trusted authority in the middle that all network participants trust. This trusted authority is called a CA or certificate authority.
Certificate Authorities : en.wikipedia.org/wiki/Certificate_authority
C.A.s work by keeping track of the entities and authenticate the public information that they provide, when a party vends his public key along with the its information. this entity's information needs to be validated before the communications can actually happens.
you can learn more about CAs and how they work by reading my previous blogpost What is HTTPS and how secure is it ?
Next Steps
In the next blog post we will begin applying these concepts to build a simple blockchain (it will be by no means production ready, but it will help explain how a blockchain works).

![[Understanding Blockchain] Part 2 : Basic Blockchain Concepts](https://cdn.hashnode.com/res/hashnode/image/unsplash/JNxTZzpHmsI/upload/v1638832184055/siV6Lr2Zf.jpeg?w=1600&h=840&fit=crop&crop=entropy&auto=compress,format&format=webp)